TEL AVIV, Israel, July 25, 2024 (GLOBE NEWSWIRE) -- Backslash Security, a modern application security solution that leverages deep reachability analysis for enterprise AppSec and product security teams, today introduced its Fix Simulation and AI-powered Attack Path Remediation capabilities. The new features equip security teams and developers with enhanced remediation guidance that is safe, secure and in the relevant context of the given application, ensuring that critical vulnerabilities can be fixed without introducing new risks.
Fix Simulation addresses a pervasive pain point faced by AppSec teams and developers: any version upgrade can introduce new risks due to unforeseen code dependencies, undoing progress and placing teams back at square one. Backslash Fix Simulation addresses this issue by simulating multiple fix options and demonstrating the resulting security posture for each one. This enables developers to save time, choose the best option, take multiple considerations into account including those unrelated to security, and avoid introducing new risks while addressing security issues
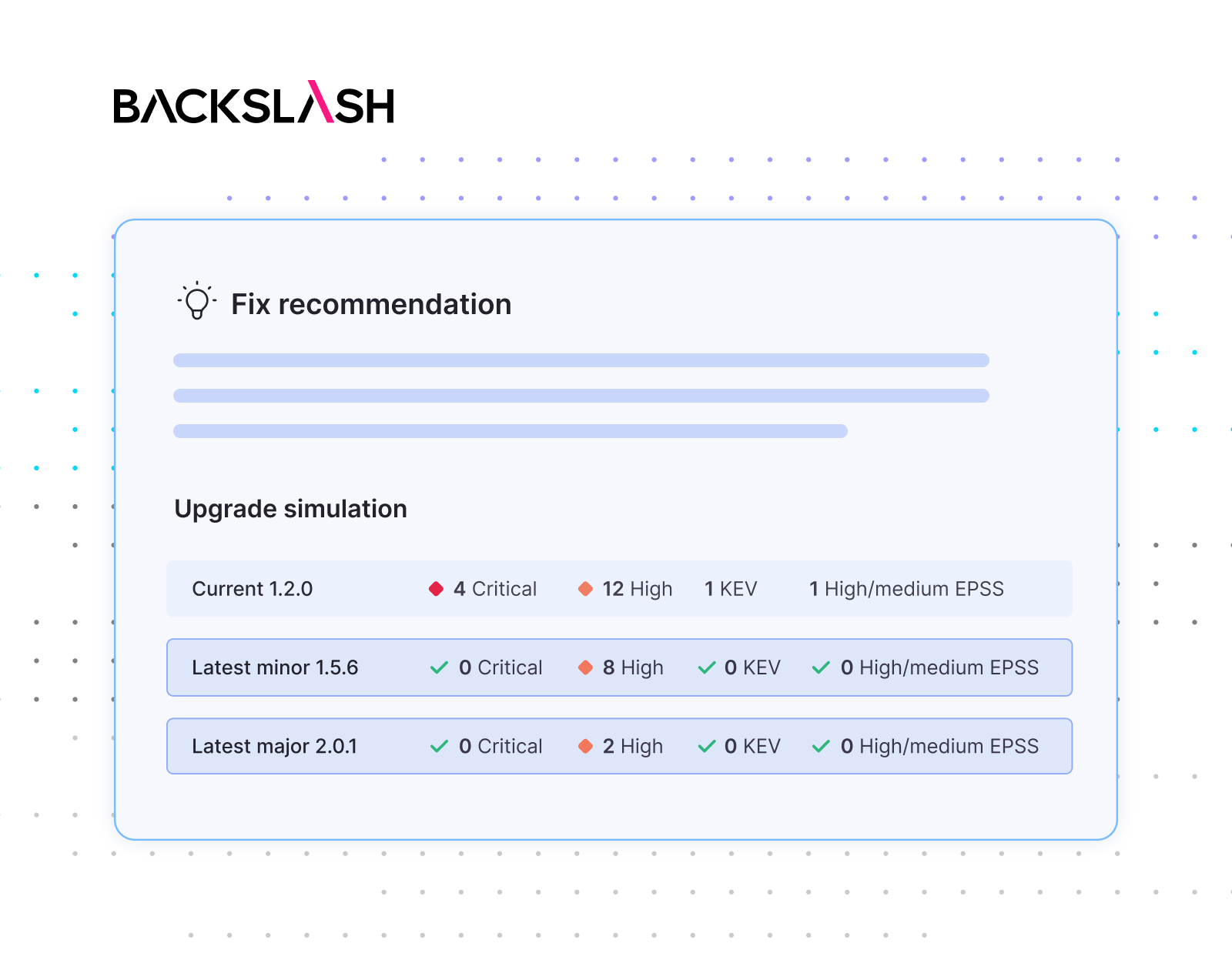
Attack Path Remediation integrates with LLMs to give developers highly contextual guidance on code vulnerability remediation, while ensuring source code stays confidential. Drawing from the comprehensive contextual insight generated via Backslash reachability analysis, the platform produces safe and secure remediation guidance. By using code metadata from Backslash scans such as technology stacks and frameworks without sharing any code snippets, organizations can leverage LLM technology while protecting against data leaks and maintaining code privacy.
“We finished the first half of the year with a record number of new customers. This reinforced our belief that it’s critical not only to focus the AppSec team on what really matters, but also to simplify the process of fixing the issues found,” said Yossi Pik, co-founder and CTO of Backslash Security. “To address this need, we developed new remediation capabilities that ensure vulnerabilities are identified, prioritized, and fixed promptly, closing the loop with tailored, context-rich recommendations. It’s like having an insider provide fix suggestions, streamlining the process for security and development teams.”
These new capabilities align with CISA’s Secure by Design Pledge requirements, providing organizations with a robust framework for maintaining security throughout the software development lifecycle. Backslash simplifies security integration into the development process, ensuring vulnerabilities are caught early and thus reducing entire classes of vulnerabilities.
Start a free trial with full access to the Backslash platform via a pre-configured demo environment that includes SAST, SCA, phantom packages, VEX, SBOM, secrets, and more, now available at backslash.security/trial.
About Backslash
Backslash's fusion of SAST and SCA empowers enterprise AppSec teams to focus on fixing only the reachable, exploitable code vulnerabilities. By identifying authentic attack paths pointed at reachable code, Backslash empowers security teams to focus on rectifying only the code and open-source software (OSS) components that are actively in use and accessible to potential attackers. Thanks to this precision, Backslash enables teams to fix only the vulnerable code and OSS that indeed needs addressing – the reachable, exploitable components.
Backed by StageOne Ventures, First Rays Venture Partners, D. E. Shaw & Co., and a roster of security veterans as angel investors, Backslash has been deployed across leading technology organizations and Fortune 100 companies. Learn more at https://www.backslash.security/.
Media Contact:
Doug De Orchis
Scratch Marketing & Media for Backslash
backslash@scratchmm.com
A photo accompanying this announcement is available at https://www.globenewswire.com/NewsRoom/AttachmentNg/9276c0b9-8732-4af9-8d49-68313bd7d24b
